Rick's b.log - 2016/08/10
You are 3.138.125.86, pleased to meet you!
Rick's b.log - 2016/08/10 |
|
| It is the 24th of November 2024 You are 3.138.125.86, pleased to meet you! |
|
mailto: blog -at- heyrick -dot- eu
The click was our "disjoncteur", the main electricity trip switch. Built in 1968, if there is any sort of disturbance (within a tolerance of 650mA) that it doesn't like, nasty transients on the line (read: lightning strikes), or if we exceed the 12kW allocation that we are paying for (out in the countryside, one pays for a certain number of kilowatts, we were originally 6kW but this meant you couldn't have the water pump kick in when the kettle and fridge were on!)... anything that upsets it - CLICK!
Sometimes it happens for no discernible reason. I consider this a "mouse peed on the wiring" event. The usual "fix" is to push the button and turn everything back on again.
I noticed my lamp was dim. I also noticed the Pi and printer had started up. I went through - noting the Livebox was booting - and told her to turn it off.
After unplugging most things, I turned on the power long enough to probe the phase that the bedrooms were on. I wasn't going to waste time probing all of the phases, this was enough to indicate a serious problem:
I called the EDF fault line. There was no reported fault in our area. So I spoke to an engineer who patiently explained that I must check the disjoncteur to ensure that the thing hadn't tripped out. In return, I patiently explained that it was off, however when I turn on I'm only seeing 130V.
A few hours later two jolly guys arrived in a big blue truck.
They probed where I had probed and confirmed things were screwy. Never mind, these old disjoncteurs, you know... So he undid the EDF-only part and probed there. Oh... hang on...
Well, at least this clears anything in our property, plus removes the excuse for anybody to arbitrarily try to pass off a Linky (so-called smartmeter) onto us.
One of the men suited up and took the cherry-picker up to the incoming lines, so see if the supply was okay (thus indicating a fault between the pole and the distribution box). The lines were not okay. Two phases down.
I took the other EDF man across the garden and said - your problem is probably over there - indicating the step-down transformer at a neighbouring farm. Or perhaps I should say the step-down transformer at a neighbouring farm that has a propensity for blowing up.
The men drove off and mom wondered why no other reports of power failures had been received. I told her about the Livebox, printer, Pi... Have you worked it out yet?
Okay, here's the thing. A filament lamp (regardless of technology) requires a certain amount of juice to make it work. If you wire a British (or French) light bulb into the American mains, it will glow dimly. If you do the reverse, it'll glow like burning magnesium until it fails. So if you turn your lights on, you might notice them being really dim. But look around the house, you'll probably see most modern gadgets working correctly. Do you have an iPad charger? Look at the bottom and you'll see it'll work on anything from 100-240V. My printer, likewise. These devices can be made for mass export with no difference whatsoever other than a country-specific power lead. The monitor that my Pi plugs into, says on the back,
The power failed just before eleven thirty. They finally had it all sorted by eight o'clock in the evening, including switching off the main high voltage line through dinner time. With that off, the entire town and all of the farms and everything connected would have been disconnected. Oh, wait, that went off at about half five. Whoo, right in the middle of milking time. Hope they had a genny to kick in and take over.
Turns out that an extremely unfortunate and largish bird either landed or took off and passed current through its body, creating an arc powerful enough to cook the bird and bring down one of the high voltage wires (either 11kV or 20kV, I forget). As a side effect, our wonky step-down transformer suffered. The low voltage was the transformer trying to cope with one of its inputs missing, I suppose we should be glad it didn't just take its default panic reaction - but then the bird had already blown itself up (poor men had to remove what was left of it from the line).
As a side effect, I'm quite pleased that the men repaired the transformer well. I'm seeing a good strong 230V on the mains. Normally it's closer to 218V. I wonder how long that'll last in the summer heat until it'll be time to invite the Photonic Induction man to say "aww, it's popped".
For the initial setup, I plugged the device directly into the Livebox. WiFi wouldn't work until the necessary stuff had been configured. The camera was rather tedious to set up because it insisted upon rebooting itself for Every. Single. Modification. It was worse than Windows 95.
Eventually I got there, and as expected with "Internet of Things", there are some issues to be aware of:
The smartphone mode just gives a really simple streaming picture (MJPEG) with controls for up, left, down, and right.
The controls at the top move the camera. The rest of the left are for configuring the video options. You can choose VGA (640×480) or QVGA (320×240) image sizes. The IR button is for turning the IR lights on and off. The arrows are for sweeping left and right, or up and down (continuously). The other buttons that look like a book and a pair of trousers (!) are for flipping the image horizontally or vertically (or both). This may be useful if the camera is mounted upside down in a dome.
For what it is worth, here is the image in its native size (the trees and fencing showing up the compression artefacts):
The camera supports having up to 16 preset locations defined. You can set one of these presets to be the 'home' position once the camera boots or reboots (settings, under PTZ).
The camera can transmit audio, but it is utterly horrible. I'm not sure whether it is over-amplified and over-compressed or what, but the best option is to simply not rely upon the microphone.
In the settings, there is apparently the option to enable some sort of motion detection, and if there is an alarm event, to email you (a picture?) and/or upload picture(s) to an FTP server. I have not experimented with either of these.
The IR light is quite powerful. This is our loft. The beam of light is because there is a place where the sun can shine in between the roof and the wall. It shows up at sunset. I think it's a hole from where a roof beam used to be, but when the roof was redone in 18-something, the beams were put in different places. Anyway, that explains the odd light. The top picture, sunset in the loft with natural light, and then again with the IR light switched on. While IR makes the image black and white (obviously!), it is actually surprisingly powerful for a few little LEDs around the camera lens.
Now, let's pull apart some of the controls. Essentially the camera provides a video stream that is a never-ending JPEG. You can get at it with the following:
Switch to QVGA size:
To switch back to VGA, param=0 and value=0. If you are playing the video, the size will change automatically. At least, it does with Firefox.
Param=14, value=1 will turn the IR light off, while value=1 will turn it on. Yes, it seems back to front.
There are plenty of other options, but none that I have the time to pull apart tonight.
However, the
It gets better. Keep reading.
Jeezuzz Christ. You're gonna want to sit down.
Doing a port scan of the camera, three ports were open and listening. 8600, 8080, and 23. I don't know what 8600 is, probably some video interface for the naffness that is the OCX (I could WireShark it, but that means running IE, so I won't). 8080 is our webserver portal. That leaves 23.
Yes. Telnet.
It starts with a dead boring login prompt that says "(none)" because the machine has no identity.
So I try my name and password. No good.
Yup. That was it.
No, wait, don't stand up. We fail harder than that. Because passwd is an unknown command. So the user data file that holds the login password is not only hardcoded to root/123456, there is no way (short of hacking the firmware directly) to be able to change this password.
Now I know you're extracting the urine. So there's this device, that has a bloody great backdoor (if it looks like a duck...), and a conveniently readable file from which can easily be read your device's MAC addresses (yellow), IP addresses (but that's no big deal, you already know that), the view-only user name and password (magenta), the freakin' admin name and password (red), plus the router's SSID and WiFi password (brown).
Holy hell, that's a whole heap of fail for a device so small.
Looking elsewhere with telnet, I can...
So this would appear to be based upon the Ralink RT5350F; a 360MHz MIPS processor with 8MiB storage and 32MiB RAM.
The storage is laid out as:
The memory is:
And it can be a quick way to check WiFi network status:
And, finally, it is nice to see they are using an up to date Linux kernel that won't be susceptible to vulnerabilities. Haha, you think?
From the inside (intranet), all bets are off. It is shamefully wide-bloody-open.
So, as is depressingly usual on Rick's b.log, it's an okay bit of low-budget hardware let down by abysmal software. Or rather, the software functions but it seems as if security (I feel sick writing that word) was sort of bolted on as an afterthought.
Bang!
So yesterday morning I was sitting on my bed with a mug of tea reading The Register when there was a loud click and everything went an eerie sort of silent.
Riiiick! came a call from the living room.
Not me! I replied.


Ah, bon...

So he undid the EDF-only (secured with a plastic crimp) holding the main supply fuses. He popped them all out and probed the incoming source. Two of the three phases were dead. Just as the house wiring would likely rise to ~380V if the neutral failed and the single phase would fail to tie relative to ground, if a phase fails the alternative is to try to spread the available power throughout the wiring. That's why I was only seeing ~130V. That's roughly 380V divided by three.

100-240V ~0.9A / 50/60Hz. So all this tech stuff will still be working. With that in mind, would a person whose kettle or microwave is acting weird not look at the TV and TV decoder still functioning and not think that the kettle or microwave is at fault? It was half eleven on a weekday. August, fair enough, but I wonder how many French housewives would pop off the power distribution cover and prod around with a multimeter? That could explain why nobody else reported a fault in the time it took for the engineers to arrive.
Cheap little webcam
The other day, a nearby supermarket was selling a motorised webcam for a "we want to shift this old stock" kind of price. It was a low-res VGA (640x480) model. I thought it might be interesting to hook this up so I could talk to mom one the phone at work while watching her do stuff. You know, like might be possible with Skype if you were able to call yourself (on different devices). Plus the motorised functions, I might hook it up in the eaves over the front door or something. Or otherwise, it might be nice to have it at the corner of the house to look across the front and down the side. I can't though, it struggles to maintain a WiFi connection in my room, never mind a solid stone wall further.
There was an HD model. It cost several times more. So I left it on the shelf.

Intro
It is essentially a cheap Chinese FOSCAM rip-off.
You can disable this (look in settings under Manufacturer's DDNS), but you may find the app won't work if you do this.
You can disable the UPnP client (in settings under UPnP), but by the time you get there, it's likely already done it. I don't know if unticking this option undoes any association (because my Livebox has UPnP disabled).
Review, sort of
There is an app. It is small. It asks for permissions that probably aren't necessary, but at least it doesn't go as far as wanting to read sensitive log data or contacts information. There is also a web interface built into the camera itself. As my Pi has laid claim to port 80, I have set the camera to respond to port 8080. Upon entry, you'll first be asked to enter the login name and password. Once you have done so, you'll see this:
The IE mode isn't worth mentioning. OCX control? Seriously?
The Firefox mode (which also works with phones and tablets), is the better option. Here, the controls look like this:
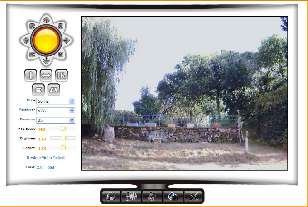

There is no option to disable the microphone. If you don't want anything to be heard, you'll need to void your guarantee and disconnect the thing the hardware way.
There is a speaker port, so you can apparently talk to your computer and the data will be sent back to the camera. I have not tried this.


Playing with the API
Looking at the interface, once you have logged into the device (standard browser auth), you can call "login.cgi" to read who you are, because even though auth is used, pretty much every request to "do stuff" requires the username and password to be suffixed to the URL. So "login.cgi" returns the following:
var loginuser="username";
var loginpass="password";
var pri=255;
"pri" is 255 for the administrator and 1 for a viewer. There's a third option (operator), but I don't know how that differs from one or the other of the previous choices.
http://192.168.1.123:8080/videostream.cgi?loginuse=USERNAME&loginpas=PASSWORD
Of course, amend the IP address, username, and password as applicable. And note passing the information in CLEAR TEXT. A clever idea over the public internet, no?
http://192.168.1.123:8080/camera_control.cgi?loginuse=USERNAME&loginpas=PASSWORD¶m=0&value=1
The camera should reply with var result="ok";.
Yet another IoT security warning
Requesting get_status.cgi will return some fairly innocuous things that can identify the camera:
var alias="IPCAM";
var deviceid="MCL-123456-ABCDE";
var sys_ver="51.3.0.152";
var now=1470848610;
var alarm_status=0;
var upnp_status=3;
var dnsenable=1;
var osdenable=0;
var syswifi_mode=1;
var mac="78:A5:DD:00:00:00";
var wifimac="78:A5:DD:00:00:00";
var dns_status=2;
var authuser=0;
var devicetype=12345678;
var devicesubtype=0;
var externwifi=0;
get_params.cgi script will drop the following juicy information:
var now1=1470848610;
var tz=-3600;
var ntp_enable=1;
var ntp_svr="time.nist.gov";
var dhcpen=0;
var ip="192.168.1.123";
var mask="255.255.255.0";
var gateway="192.168.1.1";
var dns1="8.8.8.8";
var dns2="192.168.1.1";
var port=8080;
var dev2_host="";
var dev2_alias="";
var dev2_user="";
var dev2_pwd="";
var dev2_port=0;
var dev3_host="";
var dev3_alias="";
var dev3_user="";
var dev3_pwd="";
var dev3_port=0;
var dev4_host="";
var dev4_alias="";
var dev4_user="";
var dev4_pwd="";
var dev4_port=0;
var dev5_host="";
var dev5_alias="";
var dev5_user="";
var dev5_pwd="";
var dev5_port=0;
var dev6_host="";
var dev6_alias="";
var dev6_user="";
var dev6_pwd="";
var dev6_port=0;
var dev7_host="";
var dev7_alias="";
var dev7_user="";
var dev7_pwd="";
var dev7_port=0;
var dev8_host="";
var dev8_alias="";
var dev8_user="";
var dev8_pwd="";
var dev8_port=0;
var dev9_host="";
var dev9_alias="";
var dev9_user="";
var dev9_pwd="";
var dev9_port=0;
var user1_name="USERNAME";
var user1_pwd="USERPASS";
var user2_name="";
var user2_pwd="";
var user3_name="ADMINNAME";
var user3_pwd="ADMINPASS";
var user4_name="";
var user4_pwd="";
var user5_name="";
var user5_pwd="";
var user6_name="";
var user6_pwd="";
var user7_name="";
var user7_pwd="";
var user8_name="";
var user8_pwd="";
var wifi_enable=1;
var wifi_ssid="ROUTER_SSID";
var wifi_mode=0;
var wifi_encrypt=0;
var wifi_authtype=4;
var wifi_defkey=0;
var wifi_keyformat=0;
var wifi_key1="";
var wifi_key2="";
var wifi_key3="";
var wifi_key4="";
var wifi_key1_bits=0;
var wifi_key2_bits=0;
var wifi_key3_bits=0;
var wifi_key4_bits=0;
var wifi_wpa_psk="12345678901234567890123456";
var wifi_channel=0;
var pppoe_enable=0;
var pppoe_user="";
var pppoe_pwd="";
var upnp_enable=1;
var ddns_service=0;
var ddns_proxy_svr="";
var ddns_host="";
var ddns_user="";
var ddns_pwd="";
var ddns_proxy_port=0;
var ddns_mode=0;
var ddns_status=2;
var mail_sender="";
var mail_receiver1="";
var mail_receiver2="";
var mail_receiver3="";
var mail_receiver4="";
var mailssl=0;
var mail_svr="";
var mail_user="";
var mail_pwd="";
var mail_port=0;
var mail_inet_ip=0;
var ftp_svr="";
var ftp_user="";
var ftp_pwd="";
var ftp_dir="";
var ftp_port=0;
var ftp_mode=0;
var ftp_upload_interval=0;
var ftp_filename=6448368;
var alarm_motion_armed=0;
var alarm_motion_sensitivity=5;
var alarm_input_armed=0;
var alarm_ioin_level=0;
var alarm_mail=0;
var alarm_iolinkage=0;
var alarm_ioout_level=0;
var alarm_upload_interval=0;
var alarm_presetsit=0;
var alarm_snapshot=0;
var alarm_record=0;
var alarm_schedule_enable=0;
var alarm_http=0;
var alarm_http_url="";
var alarm_audio_level=0;
var alarm_schedule_sun_0=0;
var alarm_schedule_sun_1=0;
var alarm_schedule_sun_2=0;
var alarm_schedule_mon_0=0;
var alarm_schedule_mon_1=0;
var alarm_schedule_mon_2=0;
var alarm_schedule_tue_0=0;
var alarm_schedule_tue_1=0;
var alarm_schedule_tue_2=0;
var alarm_schedule_wed_0=0;
var alarm_schedule_wed_1=0;
var alarm_schedule_wed_2=0;
var alarm_schedule_thu_0=0;
var alarm_schedule_thu_1=0;
var alarm_schedule_thu_2=0;
var alarm_schedule_fri_0=0;
var alarm_schedule_fri_1=0;
var alarm_schedule_fri_2=0;
var alarm_schedule_sat_0=0;
var alarm_schedule_sat_1=0;
var alarm_schedule_sat_2=0;
var alarmsvr=0;
Thankfully it is clever enough to stop at dev9_port for non-admin users. However admin level users can extract all of the information. And note that this includes the passwords in plain text, the WiFi security key, all of your email/ftp credentials (if you have them)...
Stupidity abounds
If it is not bad enough that the session management is the absolutely genious idea of sending the user name and password with every GET request, in clear text no less, we can actually fail even harder than that.
Trust me. Sit down.
Then I try admin and 123456. No good.
So, okay, let's try root and admin. Nope, not that either.
Wait, don't tell me... root and 123456.
The username is root and the password is 123456.
So now that anybody can log into the machine, it's a bit of a doddle to get important information:
# cat /system/www/system.ini
MCL-123456-/ABCDEIPCAMÿ?378:A5:DD:00:00:00??78:A5:DD:00:00:00?能W± ?time.nist.g
192.168.1.123255.255.255.0192.168.1.18.8.8.8192.168.1.1É???USERNAMEUSERPASSADMINN
AMEADMINPASS??ROUTERSSID.YOURWPA2KEY?PCAM6608123456789192.168.246.1255.255.255.01
92.168.246.2192.168.246.254??SOMERANDOMJUNK#
# cat /proc/cpuinfo
system type : Ralink SoC
processor : 0
cpu model : MIPS 24K V4.12
BogoMIPS : 239.10
wait instruction : yes
microsecond timers : yes
tlb_entries : 32
extra interrupt vector : yes
hardware watchpoint : yes
ASEs implemented : mips16 dsp
VCED exceptions : not available
VCEI exceptions : not available
# df
Filesystem 1k-blocks Used Available Use% Mounted on
rootfs 3008 3008 0 100% /
/dev/root 3008 3008 0 100% /
/dev/mtdblock6 3072 2512 560 82% /system
/dev/mtdblock7 512 248 264 48% /param
#
# cat proc/meminfo
MemTotal: 29344 kB
MemFree: 10308 kB
Buffers: 1032 kB
Cached: 4472 kB
SwapCached: 0 kB
Active: 5672 kB
Inactive: 4084 kB
SwapTotal: 0 kB
SwapFree: 0 kB
Dirty: 0 kB
Writeback: 0 kB
AnonPages: 4280 kB
Mapped: 1504 kB
Slab: 5316 kB
SReclaimable: 636 kB
SUnreclaim: 4680 kB
PageTables: 304 kB
NFS_Unstable: 0 kB
Bounce: 0 kB
CommitLimit: 14672 kB
Committed_AS: 9504 kB
VmallocTotal: 1048404 kB
VmallocUsed: 2720 kB
VmallocChunk: 1044644 kB
#
# iwlist ra0 scanning
ra0 Scan completed :
Cell 01 - Address: 00:00:00:00:00:00
Protocol:802.11b/g/n
ESSID:"Livebox-1234"
Mode:Managed
Frequency:2.437 GHz (Channel 6)
Quality=100/100 Signal level=-25 dBm Noise level=-92 dBm
Encryption key:on
Bit Rates:54 Mb/s
IE: IEEE 802.11i/WPA2 Version 1
Group Cipher : CCMP
Pairwise Ciphers (1) : CCMP
Authentication Suites (1) : PSK
Cell 02 - Address: 00:00:00:00:00:00
Protocol:802.11b/g/n
ESSID:"orange"
Mode:Managed
Frequency:2.437 GHz (Channel 6)
Quality=76/100 Signal level=-60 dBm Noise level=-92 dBm
Encryption key:off
Bit Rates:54 Mb/s
#
# cat /proc/version
Linux version 2.6.21 (root@mailzxh-desktop) (gcc version 3.4.2) #636 Fri Nov 16
10:03:21 CST 2012
In summary
It is a shame that the PTZ control does not offer any way to restrict its movement, because the camera head can rotate nearly 360°, you might prefer to allow certain areas to be seen but lock out others.
From the outside world, its security depends upon where you are. You can close the device off from prying eyes if you change the passwords and use a viewer-only level login. Unfortunately the passing of login information with every GET request means that you simply cannot access this device on a public AP. I have set up a VPN for situations like this, and places that don't allow VPNs, I switch to phone tethering. This still has problems because many western countries have politicians that are in favour of wholesale recording of web "metadata", and GET requests (the stuff you fetch) is metadata. Problem is, when the URL contains the login credentials, it then becomes sensitive metadata. So if you access your device remotely, don't use the admin login, use the visitor one.
Some more time and attention to detail could have made a pretty nice little clone of the FOSCAM. Instead, it is about what you'd expect. On the other hand, it does actually work (and the IR range is impressive), so that's a step up from some cheap devices.
David Pilling, 12th August 2016, 01:34
Smart meters are on the way here - interesting that they work off the mobile phone network - what you have no signal where the meter is - yup they don't necessarily work for everyone.David Pilling, 26th August 2016, 18:14
images/20160810ipcam_no_ir.jpegRick, 27th August 2016, 10:42 Rick, 27th August 2016, 18:36
Thanks for reporting this.David Pilling, 31st August 2016, 18:33
Permissions?
I use Chrome. I could easily have got an error message for you from the programmers console ctrl+shift J (similar in other browsers). But I just assumed they were missing.Steve Graham, 20th January 2017, 15:37
I tried the user/pass combinations I'd created in the web UI but they weren't accepted, so I did an internet search to find the right ones.
"root/123456". Good grief.Steve Graham, 20th January 2017, 18:39
When I logged in to the camera, I found it's creating a temporary FTP script which tries to "cd /" before uploading the image.
My FTP daemon, pure-ftp, includes a chroot option to keep access within the user's home directory, so "cd /" now works.Rick, 27th February 2018, 19:41
Thanks for the info about the cd / thing. I was wondering why trying to upload to my Orange website (uses FTP) kept failing.
That said - please read my blog entry of 2017/06/17, you might want to chuck the camera in the bin if it has the same horribly serious flaw...
| © 2016 Rick Murray |
This web page is licenced for your personal, private, non-commercial use only. No automated processing by advertising systems is permitted. RIPA notice: No consent is given for interception of page transmission. |