Rick's b.log - 2016/12/08
You are 3.128.205.92, pleased to meet you!
Rick's b.log - 2016/12/08 |
|
| It is the 28th of February 2025 You are 3.128.205.92, pleased to meet you! |
|
mailto: blog -at- heyrick -dot- eu
That said, it is possible to get some information out of the device using NetSurf.
The first thing you must do is log in. Go to http://vonets.cfg/a.asp from the machine that the Vonets is connected to. You should see the following:
For some information, go to http://vonets.cfg/adm/status.asp and you'll see this:
To see what hotspots are available (and/or signal strength), go to http://vonets.cfg/goform/get_web_hotspots_list.
One for the nerds now - http://vonets.cfg/goform/getMemoryStatus which will reply:
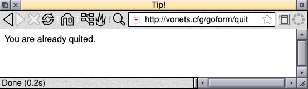
When you're done, you should go to http://vonets.cfg/goform/quit to log out (only one login at a time is permitted). The response will be a rather appallingly translated "You are already quited"!
Note that if you send a few (how many? two?) bogus requests, the built in server will simply stop responding, period. I'm not sure if this is a "safety feature" or if the server actually crashes or something. To be honest, knowing what IoT hardware is like, my money is on the latter choice.
Day Eight
Getting information from a Vonets WiFi adaptor under RISC OS
The Vonets VAP11G WiFi adaptor comes in two flavours. The original, which uses a weird custom protocol and a setup program that only works on Windows XP... and the shiny new revised that is a proper sort of gateway, has its own IP address, and a web-based configuration.
Configuration will probably need to be done on a PC, or perhaps a tablet? The Vonets makes heavy use of scripting.
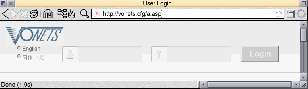
admin and admin. Then click the button on the right.
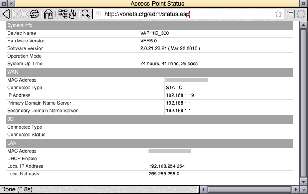
This will reply something akin to:
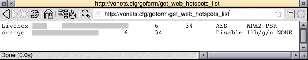
Access point SSID
[tab]
MAC address of AP
[tab]
WiFi channel
[tab]
Signal strength (0-100)
[tab]
Authentication (if any)
[tab]
Encryption type ("Disable" if none)
[tab]
WiFi mode
[tab]
"NONE" (always says that...?)
The "get_web_hotspots_list" will always perform a scan to see what hotspots are available. If you just want to see the results of the most recent scan without looking again, suffix '2' (ie get_web_hotspots_list2).
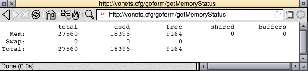
:-/
If this happens, you'll need to power-cycle.
No comments yet...
| © 2016 Rick Murray |
This web page is licenced for your personal, private, non-commercial use only. No automated processing by advertising systems is permitted. RIPA notice: No consent is given for interception of page transmission. |